LISTCRIME.COM
THE COUNTERMEASURES OF INTERNET PROTOCOL RESOURCES, LAYER 9A
The Countermeasures of Internet Protocol Resources, Layer 9A
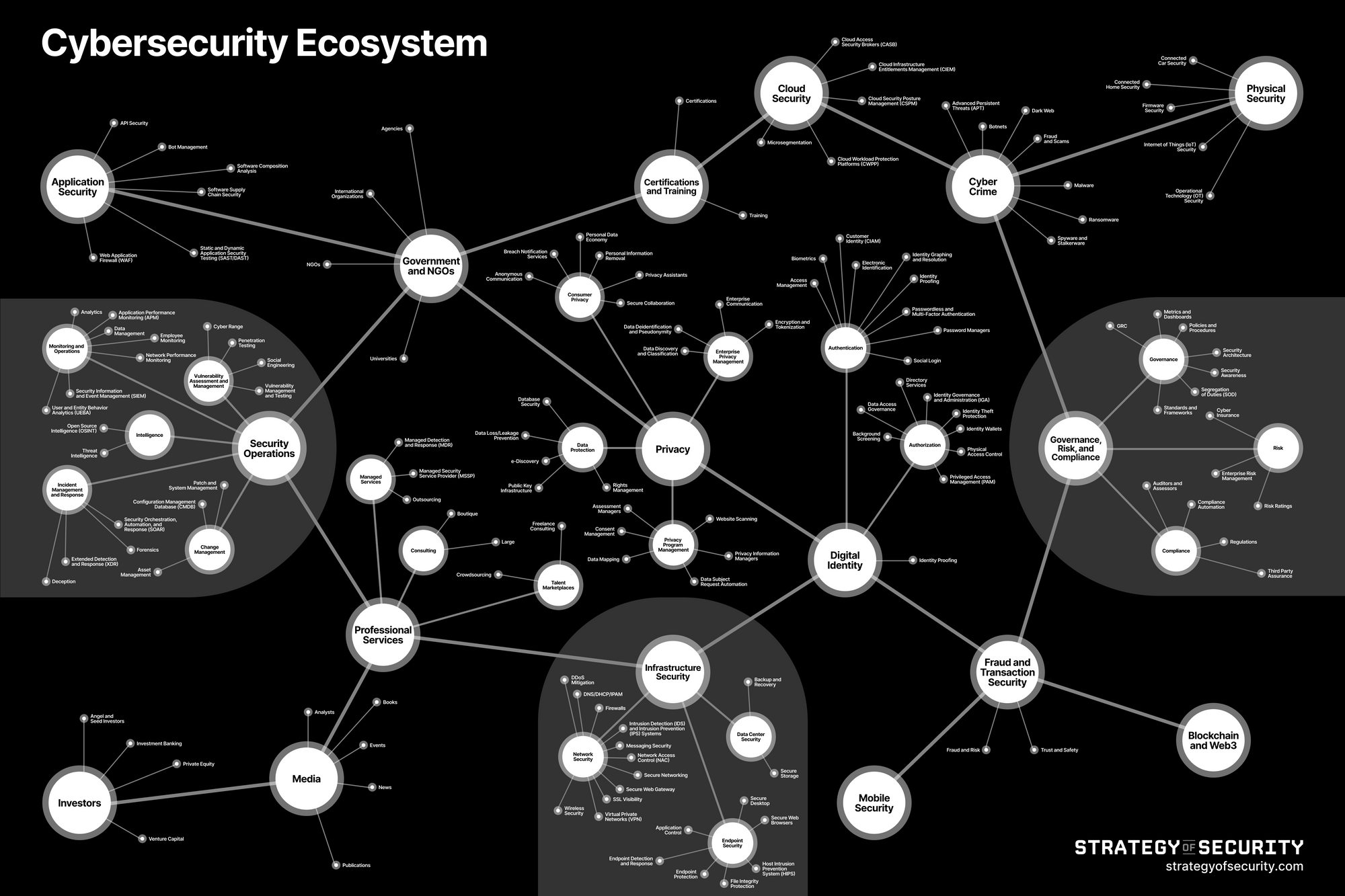
The Countermeasures used to secure Internet Protocol Resources are described as (Source NIST) protective measures prescribed to meet the security objectives (i.e., confidentiality, integrity, and availability) specified for an information system. Safeguards may include security features, management controls, personnel security, and security of physical structures, areas, and devices. 1. Technology - Security Products 2. People - Security Services 3. Process – Security compliance, regulation, and requirements. See: Nonprofit Cyber is a coalition of implementation-focused cybersecurity nonprofits to collaborate, work together on projects, voluntarily align activities to minimize duplication and increase mutual support, and link the community to key stakeholders with a shared communication channel.